
SAS Solution can help your organization strategize, develop and build a Next Generation Security Operations Center – SOC 2.0 to protect your information assets whilst counteracting the ever changing threat landscape.
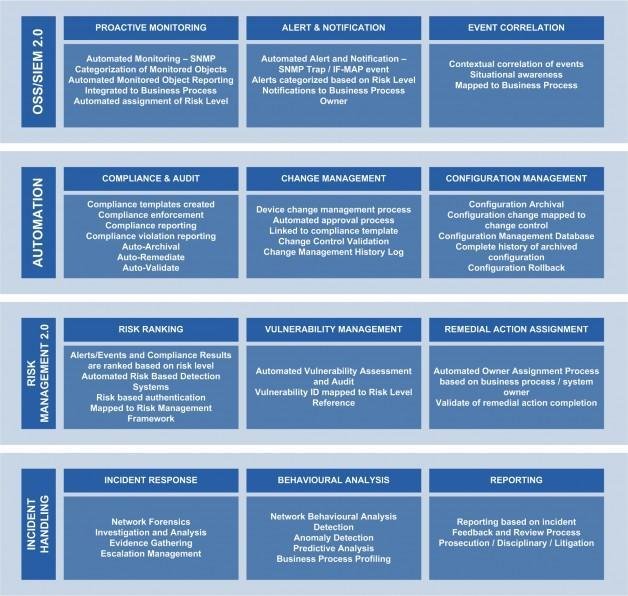
Each of the above elements interact with one another to create a comprehensive workflow for SOC 2.0 operations. Without doubt ‘people’ operating the SOC 2.0 environment play a major role in the day to day operations; either working as part of a dedicated team or a virtual team. However the efficient and effective way in which technology is deployed single handedly determines how optimized the entire SOC 2.0 process flow actually is.
Sign up to our newsletter, so you can be the first to find out the latest news and tips about Cyber Security Programs, as well as general Chevening updates throughout the year.

P.O. Box: 123, Postal code: 111,
Al khuwair, Sultanate of Oman